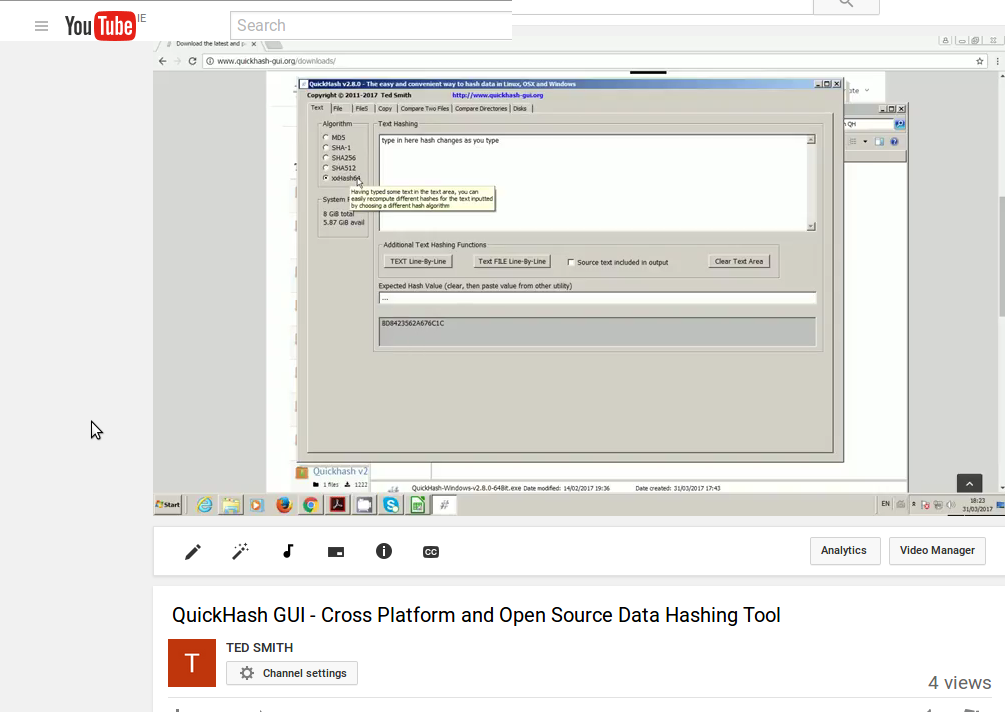
Base64 Decoding and Hashing Coming Soon
v2.8.3 has been in development for a few weeks and I was about to start thinking about getting it compiled and released, but then one user contacted me with quite a unique and good idea that I hadn't thought of before...Base64 decoding. As you may know, Base64 encoding can be used to convert files like PDF e-mail attachments and picture files into a form of non-binary data that is text based. Base64 is basically groups of 4 text characters that typically ends with an '=' or '==' character. Once decoded, the original file can be used as normal. So [...]